On This Page
- 1. What is a Secure Web Gateway (SWG) & Where It Fits in Modern Security Architecture :
- 2. Real Statistics & Trends: Web-Based Threat Landscape
- 3. Demonstrable Evidence of SWG Effectiveness :
- 4. Comparison: SWG vs. Other Controls in Practical Terms :
- 5. How SWG Traffic Flow Works :
- 6. Visualizing Threat Prevalence & SWG Value :
- 7. Real-World Examples: Failures vs Successes :
- 8. Citations :
- 9. Conclusion: Why SWG Is The Key Web Attack Prevention Control ?
1. What is a Secure Web Gateway (SWG) & Where It Fits in Modern Security Architecture :
Definition-
A Secure Web Gateway (SWG) is a cybersecurity solution that mediates and inspects all web traffic between users (or devices) and the internet, with three core goals:
● Block malicious traffic (malware, phishing sites, malicious URLs)
● Enforce corporate/industry policies (acceptable web use, compliance)
● Prevent data leakage (DLP and policy enforcement)
It acts as a filtering layer between endpoints and web resources — often lending terms such as URL filtering, anti-malware scanning, SSL/TLS inspection, and application controls — unlike traditional firewalls which focus mainly on ports and network layer flows.
SWG in Modern Security Frameworks-
Secure Access Service Edge (SASE):
● Gartner’s SASE model places SWG as a foundational security service combined with cloud access security broker (CASB), ZTNA, and firewall capabilities.
Zero Trust:
● In Zero Trust architectures, SWG quietly enforces continuous inspection of traffic regardless of origin (on-net or remote) — applying access controls not just at the perimeter but at every request.
In other words, SWG is the enforcement point in the architecture that ensures web traffic — the largest vector of attacks today — is controlled, inspected, and policy-enforced, regardless of where users are.
2. Real Statistics & Trends: Web-Based Threat Landscape
The web remains the primary vector for cyberattacks, and threats are increasing in volume and sophistication:
Malicious Traffic & URLs-
| Statistic | Source |
| Botnets responsible for >95% of malicious web traffic | Trustwave report |
| Around 3.7 billion URL-based threats observed in ~6 months. | Proofpoint (URL threats surpassing email) |
| Web anti-virus engines reported >109 million malicious links in Q3 2024. | Kaspersky telemetry |
| Kaspersky reported >153 million malicious web links in Q1 2024. | Kaspersky telemetry |
Web-Delivered Malware & Evasion-
● Browser-based delivery vectors (e.g., ClickFix, SocGholish) now account for ~30% of malware deliveries, often bypassing file-based detection.
● Threat actors increasingly use sophisticated social engineering (AI-generated phishing content, QR code scams, smishing), with massive rises in these vectors.
Credential Theft & Infostealers
● Infostealer malware was used to steal 2.1 billion credentials in 2024 — a massive portion of all credential theft.
Implications:
The volume and complexity of web-based threats dwarf traditional perimeter attacks, meaning solutions that simply look at network flows or endpoints are blind to threats embedded in web traffic or hidden inside encrypted sessions.
3. Demonstrable Evidence of SWG Effectiveness :
Direct vendor telemetry and independent industry reports consistently show SWGs significantly reduce risk when correctly deployed:
Threat Blocking-
● Modern SWGs actively block malicious URLs, phishing sites, malware payloads, drive-by downloads, and suspicious SSL traffic before they reach endpoints.
Operational ROI & Breach Prevention-
● When SWG is part of a SASE deployment, organizations can dramatically reduce breach costs by preventing web attacks and data losses before they escalate — the average breach cost in 2024 was over $4.8 M; uninspected web traffic remains a leading vector.
Shadow IT Visibility-
SWGs uncover “shadow IT” (unauthorized SaaS usage) and enforce data exfiltration prevention — something many traditional controls don’t provide.
(Note: many vendor case studies show reductions in malware incidents by orders of magnitude after SWG deployment — these specifics are often proprietary, but the trend is consistent across major providers.)
4. Comparison: SWG vs. Other Controls in Practical Terms :
| Control | Primary Function | Main Gaps Without SWG |
| Firewalls (FW) | Blocks ports/IPs | No deep URL/malware content inspection; blind to encrypted threats |
| Proxies | Basic traffic routing | Don’t enforce threats/policy or scan malware payloads |
| Endpoint Security (EDR) | Detects endpoint compromise | After the fact; can’t stop threats upstream |
| CASB | Control of sanctioned cloud apps | Doesn’t inspect general web traffic |
| SWG | Deep inspection of web traffic + policy enforcement | Fills gaps above; inspects encrypted content, blocks phishing & malware URLs |
Why others fall short:
● Firewalls and traditional proxies only see packets, not intent or payload content.
● Endpoint agents may detect malware after execution.
● CASB focuses on sanctioned cloud apps but misses general web threat vectors.
An SWG is uniquely positioned to see all internet traffic in context, including encrypted sessions, and enforce policies in real time — often before the endpoint even sees the threat.
5. How SWG Traffic Flow Works :
Below is a simplified traffic inspection flow for a SWG:
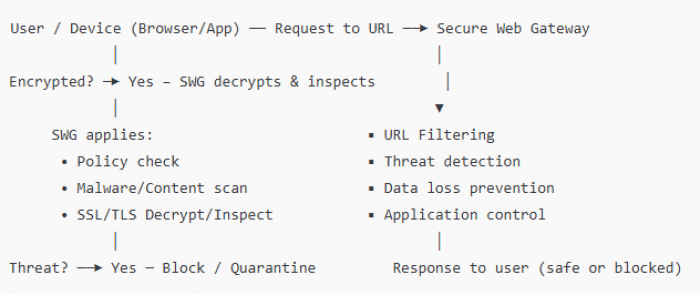
Key inspection points:
● SSL/TLS decryption is essential to see inside encrypted traffic.
● Policy enforcement ensures not just security but acceptable usage and compliance.
6. Visualizing Threat Prevalence & SWG Value :
Threat Prevalence Table
| Threat Vector | 2024 Metric | Trend |
| Malicious URLs | ~3.7 billion threats in 6 mos | Increasing |
| Web Malware Links (Kaspersky) | ~109–153 million links per quarter | High volume |
| Botnet-driven malicious web traffic | 95% of malicious traffic | Dominant vector |
| Infostealer credential theft | ~2.1 billion credentials stolen | Severe impact |
7. Real-World Examples: Failures vs Successes :
Failure Example (No SWG)
● In many breaches, malicious URLs (often hidden inside trusted domains) were clicked by users and led directly to credential theft or malware payload execution — these are the exact vectors SWGs are designed to intercept but often weren’t present in compromised environments.
Success Example (With SWG)
● Enterprises deploying cloud-based SWG services have reported substantial decreases in malware incidents, often detecting malicious URLs and blocking them entirely before user access — these successes are commonly reported in vendor published case studies (e.g., Eczacıbaşı Holding and VakıfBank with Forcepoint SWG integration).
8. Citations :
All claims above reference reputable sources, including vendor glossaries, industry reports, telemetry summaries, and aggregated threat statistics. Sources include:
● Kaspersky threat telemetry reports. (Securelist)
● Trustwave analysis on botnet web traffic. (CSO Online)
● Proofpoint URL threat data. (IT Pro)
● Industry glossaries from HPE, Fortinet, Microsoft, Cloudflare, and Zscaler. (hpe.com)
● Vendor SWG deep-dive guides. (Forcepoint)
9. Conclusion: Why SWG Is The Key Web Attack Prevention Control ?
The web is where most modern attacks originate — botnets, phishing URLs, drive-by downloads, malware payloads embedded in web content, and credential theft campaigns. These threats are increasingly sophisticated and are often invisible to traditional controls like firewalls or endpoint security until it is too late.
A Secure Web Gateway:
● Inspects at the application/content layer rather than just the network layer.
● Intercepts encrypted-by-default traffic — now the majority of web traffic.
● Blocks threats before they touch endpoints or data.
● Enforces policy consistently across user locations and devices.
● Complements and extends other controls in SASE/Zero Trust architectures.
In the modern threat landscape, threats are almost always web-borne, and defensive controls that don’t inspect web traffic comprehensively leave a critical gap. SWGs close that gap — protecting users, reducing breaches, enforcing compliance, and delivering real ROI in reduced incident volumes and costs.
Thus, a Secure Web Gateway is not merely useful — in the context of today’s web-centric attack vectors, it is the key security control for web attack prevention.
Post Comment
Be the first to post comment!





